19 Best Security Tools for Protecting Your Apps & Websites 2024
Security is an ever-emerging topic, with numerous high-profile breaches happening every day. There’s a big reason why new startups focus on security issues and so many developers are cautious about global network security. The FBI, the CIA, and the country wars are testaments to the scale of hacking happening worldwide. But it’s not just the big networks that need protection, it’s also your applications and websites that need to be secured, and protected against unauthorized access. Because the web is so huge, it’s hard to keep track of everything happening within your app, your app, and not to mention your servers. You need help, and we are here for you!
More on Web Security
These amazing startups are here to help you out with your security concerns. The number of platforms that have risen from the ground up in recent years is staggering and flattering. That is because at one point during the web’s upbringing, security was a scarce topic; nobody bothered about it. Websites, communities, and softwares were easily being hacked into. User data were carried to the dark market and sold to the right buyers. Although, that doesn’t mean that this isn’t happening globally; it probably is more than ever, but with greater secrecy. What matters is the overall state of security you provide to your users during the development phases of your software, apps, and websites.
Your job is to ensure that certain layers of security are provided for your users. In the unlikely event of a security breach, the data is hardened and protected to the best ability of modern software. Having the tools to check your logs and other system-related events against attacks can also unveil some unsettling information. But the sooner you get ahead of the hackers, the more pleasant your experience will be as someone who develops for the digital world. We got your back with these amazing startups that have invested their creative power to create tools and applications that will keep your digital projects sound and secure.
Best Website Security Tools
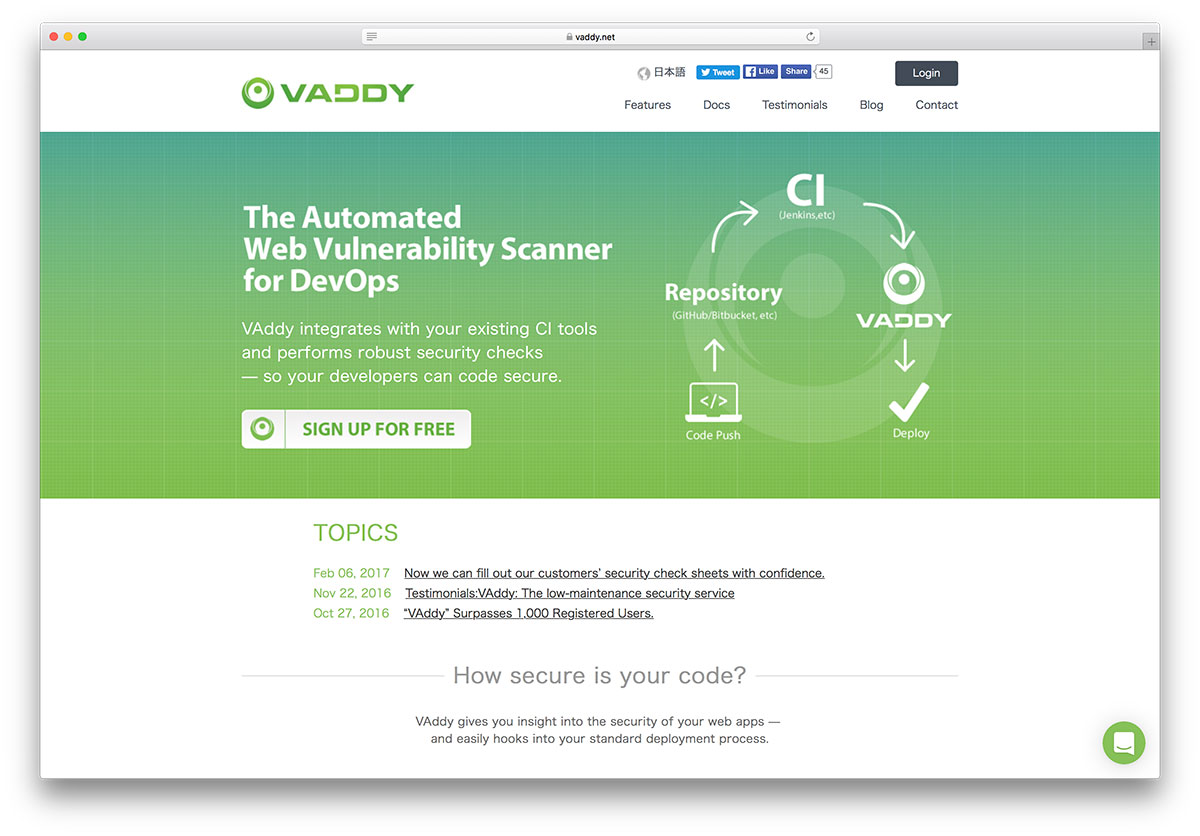
VAddy

The process of developing an application itself is so demanding for developers. Anyone can easily overlook vulnerabilities, without the clear intention of doing it. Even websites like Google, Instagram, and Facebook struggle with vulnerabilities daily. Vulnerabilities exist, sometimes in subtle ways that we won’t notice until someone points it out to us. And that’s sort of what the VAddy platform tries to do.
These security experts are building a product that will work with your codebase and analyze it for any possible vulnerabilities, before you push out your new features out in the production environment. VAddy will automatically scan any new updates you’re adding to your code. Then, it will give you a fair warning if there’s a possible vulnerability hiding anywhere. No longer will you have to scan your code manually. But the platform goes beyond the basics; the codebase can be visualized through statistics of the many vulnerabilities. You can also pinpoint which developers have caused the most bad code adds to the app itself. Not to shame anyone, but info like this is so helpful in understanding how your team works together.
Let’s Encrypt
HTTPS and SSL are now frequently-talked-about topics, and highly emphasized even by the most revered companies like Google. Not only are secure websites rewarded with better indexing rankings and better search result rankings on Google, the customers of your platforms will also be thankful to you for being cautious about security, and putting in the right measures to keep data safe and secure.
Let’s Encrypt project was born out of the necessity to protect the global web with secure SSL connections; there couldn’t be a better way to do this than by offering free SSL certifications to anyone who needs them. Mozilla, Facebook, and Shopify are amongst the leading sponsors for this project. You can rest peacefully knowing that your sites will be protected with the most hardened layers of security. Let’s Encrypt is free forever, and it is also automated. That means you can install it once and forget about it; any future security releases will automatically adjust to keep your site safe no matter the circumstances. After such large-scale web attacks in recent few years, developers and website owners must take the appropriate measures to keep their websites safe and secure for everyone.
Probely
Probely is a security tool for developers, teams, SaaS businesses, you name it. This powerful alternative is packed with amazing features to keep it all under complete control. Probely helps find issues and assists you in how to fix them, so everything is back to normal as fast as possible. You never need to wonder what is happening with your project again, let Probely take care of the scanning and reporting for your convenience.
Probely is a versatile tool that caters to numerous different objectives. Of course, you can start entirely free of charge to see how things operate. Additionally, there are three premium plans covering small businesses and large organizations. Some features include scheduled scans, blacklisting, cookie customization, 3rd-party app integrations and swift, one-minute scans. Keep security first-class at all times with Probely and be safe than sorry.
Intruder

One thing is for sure; you do not want intruders on your application or another project. Thanks to Intruder, a security tool, that’s something you can take care of quite easily. Instead of doing it all manually, make it happen with Intruder instead. In short, let the machine do all the heavy work instead of you, while you only focus on making fixes and running your project flawlessly. Intruder allows you to find weak spots before the hackers.
Intruder is here to scan your system for all sorts of stuff, like configuration and encryption weakness, missing patches, application bugs, CMS issues and heaps more. There are a whopping nine thousand security checks available. Developers, small businesses and enterprises, everyone is welcome to take Intruder to the total advantage. Save time and let your app run without a hitch.
SiteGuarding

SiteGuarding is a flexible security tool for applications and websites alike. Whether a simple blog or custom website development, even eCommerce platforms, SiteGuarding handles them all easily. With 24/7 monitoring, SiteGuarding is your project’s security that handles bugs and issues that may appear. You can immediately see what is happening with live reports and act accordingly. Even if your website got blacklisted, SiteGuarding is a solution that will help you out.
Some of the features of SiteGuarding are website antivirus, malware removals, secure web hosting, cleaning core CMS files and backups, to name a few. You can, indeed, start with the fourteen-day free plan, test things out and only then decide whether or not SiteGuarding is a fit. Still, SiteGuarding is very affordable, offering four different pricing packages, so everyone finds the one that suits their project ideally.
Sucuri
When you first launch a website or a blog, you might not think of security just yet. However, the sooner you set things up, the better for you and your project. Unfortunately, hacks and attacks do happen to almost everyone some time or another. It is just the way it is in the online world. Luckily, with the right website security tools, you can sort things out pretty quickly, feeling safe and secure that everyone will be fine.
One terrific alternative is Sucuri. It helps you fix issues and protect your project from upcoming attacks. Monitoring, protections, performance improvements, SSL support, SIEM integration, and other goodies come part of Sucuri. Of course, not all plans offer everything, but even the basic solution is a great starting point. With over seven hundred full websites cleaned daily, Sucuri is doing exceptionally well. Never run into issues again.
Qualys SSL Labs
The Heartbleed bug-tested the patience and determination of the public developer community that uses OpenSSL in their security layers. It was one of the most high profile vulnerabilities in the recent decade, leaving millions of websites and serving open to serious attacks that could have (and most likely did) caused severe damage for businesses and any other paid ventures. The SSL Server Test is a wonderful compliment to the many SSL services we already discussed (and a few more still to come). With the SSL Server Test, you can quickly assess what vulnerabilities exist on your website about SSL and what actions you must take to secure the layer strongly. All analysis are graded with an output of information on how to solve any possible vulnerabilities in your website’s SSL layer.
Qualys

OWASP is a household name when the talks come to security. The OWASP project has helped protect millions of websites. It has helped millions of developers and webmasters learn about concise security practices and tactics that must be implemented in digital security. The Qualys audit tool will analyze your web applications through the OWASP’s recommended security checklist. Then, it will give you concise insights in your level of security and explain how you can fix any potential vulnerabilities. It doesn’t hurt to run your project through this scanner occasionally to ensure that you remain on top of all the modern breaches, many of which extend daily.
OneLogin

Enterprise businesses are at higher risk than anyone and anything else. Enterprise means that much data is moving through the cloud and the server infrastructure. It’s easier for hackers to target big enterprises and collect all their data at once than to target smaller ones and work through small amounts of data to get the desired result.
OneLogin is a secure identity management platform that you can configure to create secure passwords for any platforms you’re accustomed to using on the web. OneLogin verifies your identity and gives you a one-time login passphrase that you can use to access the apps and websites that are essential to your own business. OneLogin’s catalog of more than 4,000 pre-integrated applications makes it easy to enable single sign-on and user provisioning for your enterprise applications. OneLogin proactively maintains the integrations and adds new ones daily.
Report URI

Report-URI focuses on the security of external and third-party resources added to the workflow of your apps and websites. The CSP protection enables you to create a list of external sources you would approve to be loaded externally. Any resources that aren’t on that list would be declined. This helps to prevent common attacks such as XSS — cross-site scripting. The HPKP module, in turn, protects your apps from any resources that have breached certificates. These are two deep layers of security that you can add to your apps, and are worth experimenting with to better understand how they could help keep your apps secure and healthy.
GlobalSign
As crazy as it sounds, open-source projects make the web exist. We don’t have to pay anyone to browse websites that use the Apache web server, neither do we have to pay Google for allowing us to use Chrome. These are examples of how open-source rules the web, and how it has made the web so accessible for everyone.
GlobalSign wants to reward open-source project owners with a free SSL certificate if you can prove that your project is indeed open-source, and providing value back to the community. You will need to acquire a license from the Open Source Initiative. You get a certificate from GlobalSign — a well-established SSL provider that values security on a very deep core level. GlobalSign is the leading provider of trusted identity and security solutions enabling businesses, large enterprises, cloud service providers and IoT innovators worldwide to secure online communications, manage millions of verified digital identities and automate authentication and encryption.
Auth0

You can save a ton of time by hooking your apps in the Auth0 cloud to ensure that any login management is always secure. Auth0 also specializes in identity protection for developers. Start by creating and connecting your app to Auth0, then choose the platforms you want to enable secure identification for. Add a couple of users, setup the identity rules and create a custom login page that will get the protection with the extensive layers of security that Auth0 provides.
RingCaptcha

RingCaptcha takes two-factor authentication a little further; if your data security is important to you and you wish to give users a real way of protecting themselves, why not employ this method of an verification? It involves the user receiving a message on their phone with an activation code that the phone owner himself could only verify. These security methods are becoming increasingly popular because of how personalized they are.
Duo Security
Duo is among the most revered security companies, thanks to their dedication to the craft and available resources to create more personal security layers. Their main product is the two-factor authentication that can protect apps and websites alike. The API Duo provides developers makes integrating two-step authentication within your apps and software a breeze. This is a revolutionary way of giving users the security protection they so desperately seek. Duo utilizes the mobile smartphone you’re always carrying to ensure that any app that’s protected with Duo will double check with you through personalized security checks that come directly to your smartphone. Duo follows an agile development cycle, releasing updates in hours and days compared to several months and quarters, typical of other two-factor vendors.
Crypteron
You can start securing your databases and direct application calls with various products. Crypteron is as useful for developers for agencies and enterprise-level companies. It works closely with developers to provide concise security protection for applications you build in the cloud.
Acunetix

Acunetix has existed for as long as one can remember, back in the year 2005. This was the most widely used security scanning application by both developers and script kiddies who wanted to explore common website vulnerabilities and exploit them. As it was back then, Acunetix didn’t provide a very concise overview of how vulnerabilities worked. It was rare to find big-scale exploits within a website. Today, Acunetix has a database of more than 35,000 vulnerabilities that it can check your website against; prepare to learn about some nasty stuff that hackers could do to your website. The sooner you learn about the open holes in your websites and apps, the sooner you can start protecting and securing them.
Acunetix seems also to have transitioned to a web-oriented dashboard. Back then, you had to download the full scanning suite and scan for hours at a time. Now, it’s possible to do it all on the web. The price can seem scary, but if you seek protection, the investment will quickly pay itself back through customer satisfaction and trust signals.
Foxpass
The real trouble-causing factor in the early days was that software users were given single-handed administration permission to the whole software. Anyone with a single admin account could access everything on the platform. Now, things are getting more intelligent; companies like Foxpass exist to ensure that your enterprise software accounts are given only the permissions required for their job.
It’s a smooth technique for ensuring that there’s only one main admin account on the network, and everyone else gets access to the necessary tools. Not only that, Foxpass will also closely monitor and record any access that users makes to the system. This will disallow further access to the system for that particular user. In the case of a breach, it will be fairly easy to pinpoint where the attacks are coming from. Thus, this is a universal platform that enterprises can apply to their systems and networks in many ways.
BitNinja

Opting for a security tool that offers single data protection methods is no longer reliable. Developers are looking for full spectrum solutions such as BitNinja that can combine several protection methods and consistently work through them to deliver security protection at a level never seen before. BitNinja provides common honeypot protection, enabling botnet protection to prevent nasty DDOS attacks and brute force attacks towards your submission forms. Web application security is still in early stages, but some report a good future ahead of it. Logs are recorded to give all BitNinja users insight in how the platform is securing their apps and websites. Particularly popular with cloud providers, and web hosting providers.
LoginTC
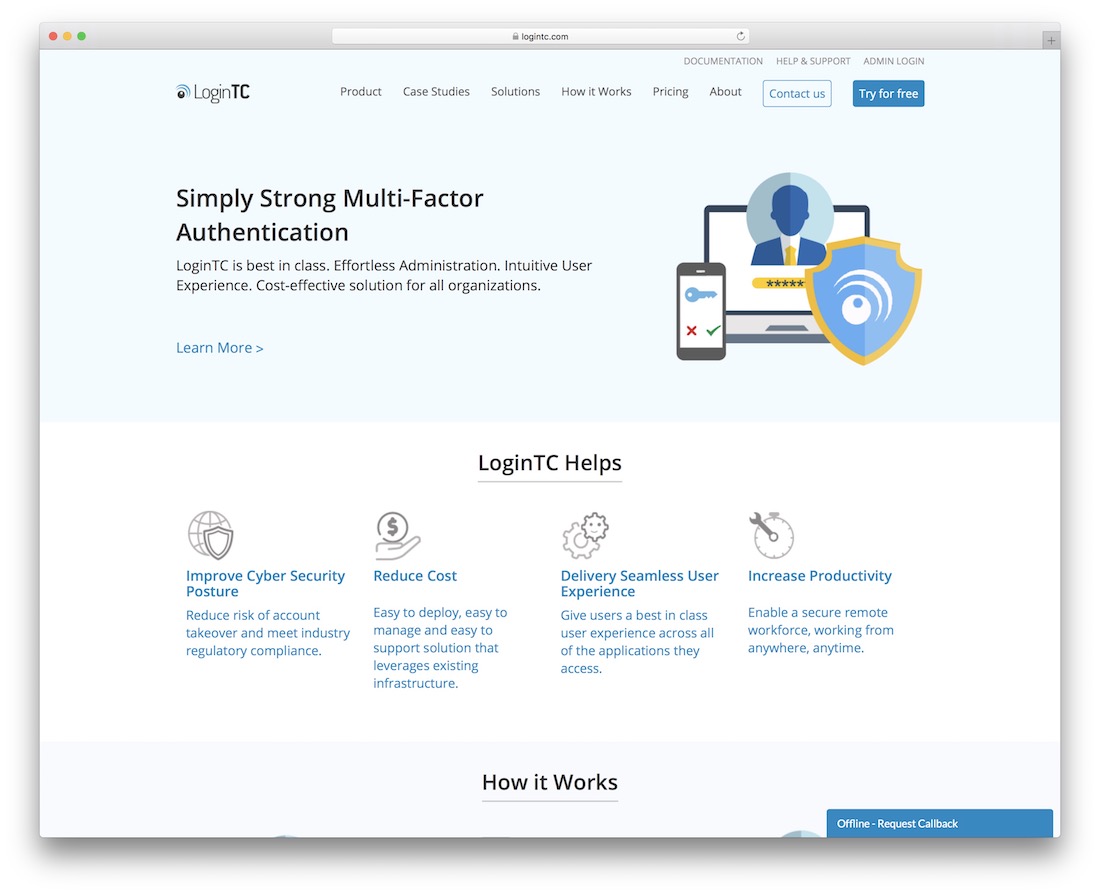
LoginTC will ask whether the user trying to access your account is you. It will provide details of the login attempt and ask you to allow or deny the connection to the app. A wonderful security layer that companies should embrace more.



Thanks for sharing a security with clear explanations, It is very easy to understand quickly.